Understanding How Envoy Sidecar Intercept and Route Traffic in Istio Service Mesh
Table of Contents

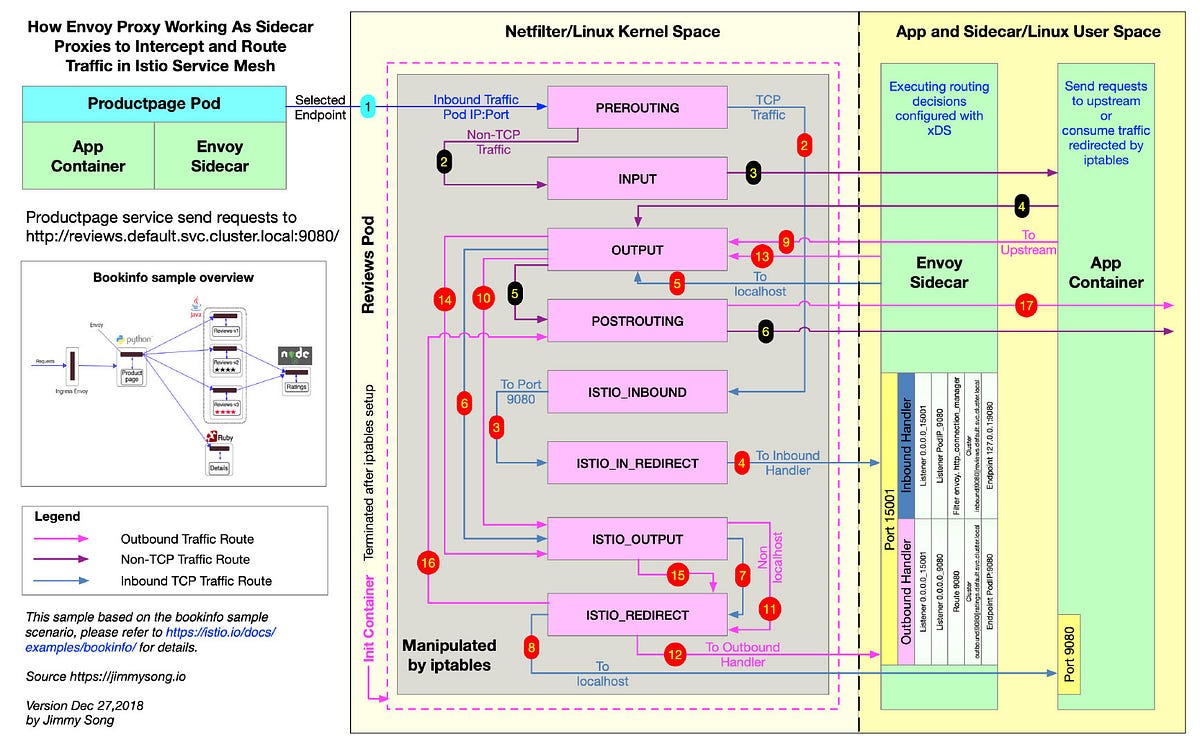
This article uses Istio’s official bookinfo example to explain how Envoy performs routing forwarding after the traffic entering the Pod and forwarded to Envoy sidecar by iptables, detailing the inbound and outbound processing. For a detailed analysis of traffic interception, see Understanding Envoy Sidecar Proxy Injection and Traffic Interception in Istio Service Mesh.
Source: medium.com

