CVE-2018-18264 Privilege Escalation Through Kubernetes Dashboard
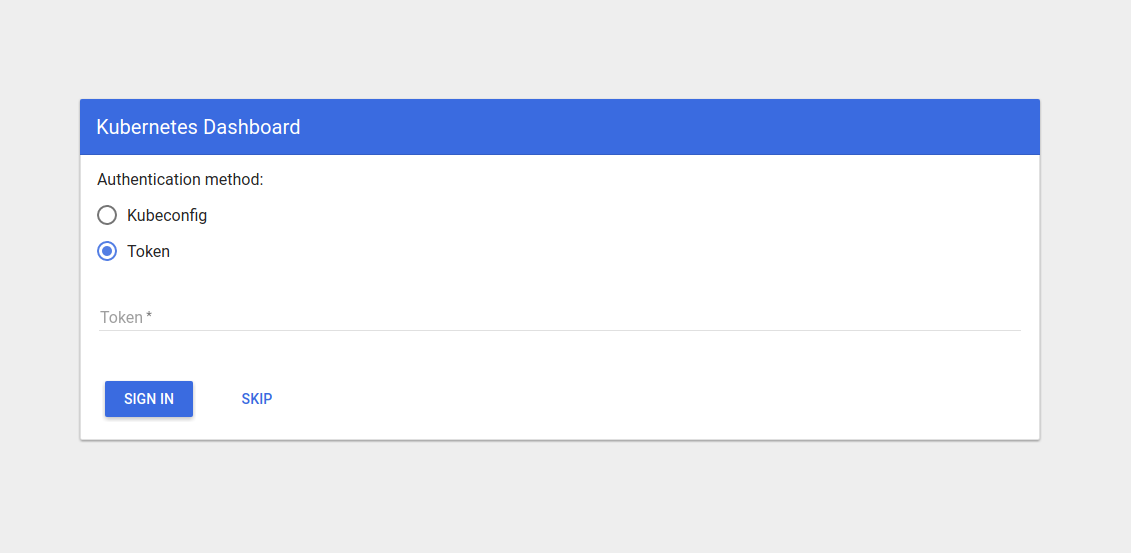
A recently disclosed vulnerability in Kubernetes dashboard (CVE-2018-18264) exposes secrets to unauthenticated users. In this blog post we’ll explore some key takeaways regarding monitoring privilege escalation on Kubernetes. The Kubernetes dashboard is a web based user interface that allows users to manage applications and resources within the cluster.
This service has a login functionality starting from Kubernetes 1.7.0. Since then, users are able to authenticate with a kubeconfig file or an access token. But it is also possible to skip the authentication altogether with a skip button.
The recently disclosed vulnerability in Kubernetes dashboard: CVE-2018-18264 allows users to escalate privileges within the Kubernetes cluster using the dashboard to potentially access information they are not actually granted access to: a user could skip the authentication and query resources that the dashboard service account has access to, like the kubernetes-dashboard-certs secret, that stores TLS certificate and private key for the service. This is particularly critical because with those TLS credentials, the attacker could impersonate the dashboard service, spawning a fake service to steal other user’s credentials.
Source: sysdig.com