Detecting the Kubernetes API Server DoS Vulnerability (CVE-2019-1002100).
Recently, a new Kubernetes related vulnerability was announced that affected the kube-apiserver. This was a denial of service vulnerability where authorized users with write permissions could overload the API server as it is handling requests. The issue is categorized as a medium severity (CVSS score of 6.5) and can be resolved by upgrading the kube-apiserver to v1.11.8, v1.12.6, or v1.13.4.
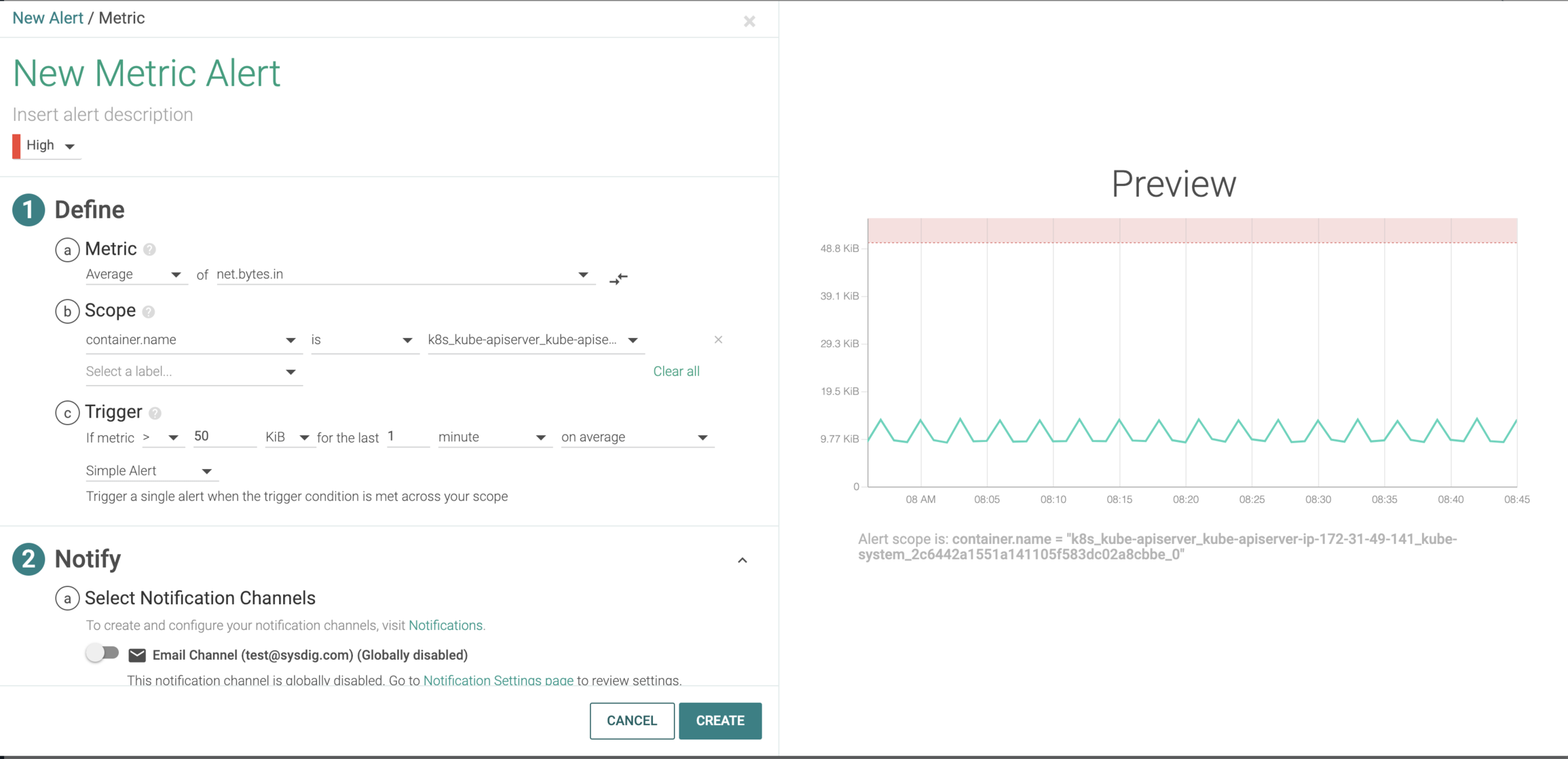
In Kubernetes, the control plane on the master node consists of the API Server, the Controller Manager and Scheduler(s). The API Server is the central management entity that directly communicates with etcd and serves the Kubernetes API used both for internal cluster communication and external communication via kubectl or other clients. Sysdig has built the only cloud-native intelligence platform that is designed to secure, monitor and troubleshoot your next-generation environment.
Users can create alerts, monitor and detect abnormal behavior, and correlate user activity to understand the entire security incident. Here we can see that the current traffic conditions are normal, but if something spikes into the red zone (abnormally high inbound traffic that hits the API server), an alert will be triggered and the appropriate teams will be notified. When would a spike happen?
A DoS attack on the API Server would lead to the server not being able to handle additional requests. This type of attack occurs at Layer 7 and it is hard to detect based on HTTP request signatures. Signature based detection works well for detecting abnormal string patterns with limited size.
The DoS attack is conducted by a malicious user whom’s be authenticated and authorized, the patch request(URI, Verb) looks normal but with abnormal payload size.
Source: sysdig.com