Effective Secrets with Vault and Kubernetes
Table of Contents

Kubernetes is the de facto standard for container orchestration and Vault by HashiCorp is the de facto standard for secrets management. Now the question is: how do you combine those technologies so that you can use secrets from your central Vault instance in your Kubernetes applications? One solution would be to use the AppRole auth method.
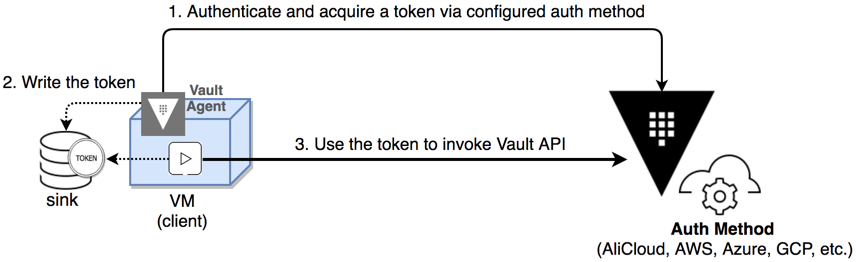
Boostport provides a nice integration of AppRoles in Kubernetes. Another possibility is to use the Kubernetes auth method. This auth method establishes a trust relationship between Vault and your Kubernetes cluster so that you can use a service account to authenticate to Vault.
You can further use the Vault agent with Kubernetes to get and renew authentication tokens. In this walk-through article, I’m going to show how you can achieve the same thing with some Go helper tools that authenticate and renew tokens and even go a step further—synchronize a predefined subset of secrets from Vault to Kubernetes.
Source: itnext.io