Secure Your Service Mesh With Istio and Keep an Eye on It With Kiali
It is important to fine-tune the set of services that a workload has access to. It is a good practice to give the least privilege. In that sense, we should grant permissions to each workload to communicate with exactly the services it needs to access.
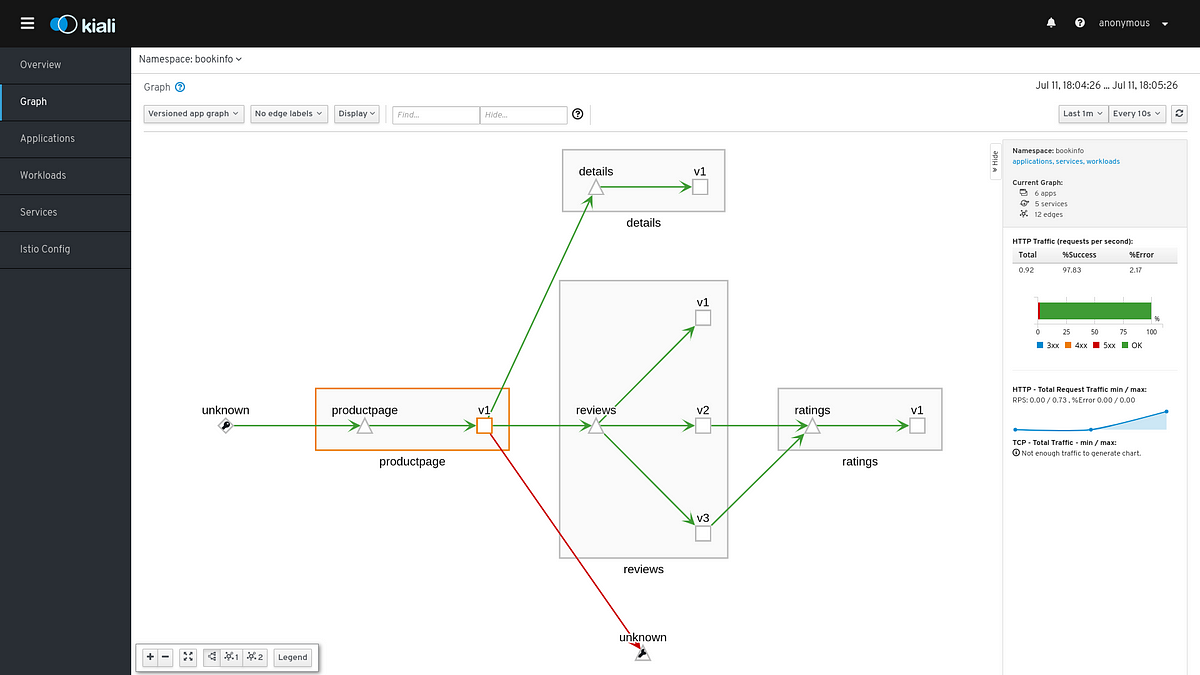
This could also help reducing the attack surface in case of a compromised workload in our mesh. Unwanted requests between servicesFor example, a developer could contact the ratings service directly instead of using the review service. Let’s simulate this by sending requests from productpage to ratings service.export PRODUCTPAGE_POD=$(kubectl get pod -l app=productpage -o jsonpath={.items..
metadata.name})kubectl exec -it $PRODUCTPAGE_POD -c productpage — python -c ‘import requests;r = requests.get(‘http://ratings:9080/ratings/0’); print r;print r.json()’You should get a similar message to let you know that the request succeeded{u’ratings’: {u’Reviewer2′: 4, u’Reviewer1′: 5}, u’id’: 0}After waiting for some seconds, we can refresh the graph and see the request from productpage to ratings.
Source: medium.com