Controlling Outbound Traffic From Kubernetes
We recently finished a major networking project which let us control internal traffic in our platform. And we’ve been thinking about how we can add similar security to network traffic leaving our platform. At Monzo, the Security Team’s highest priority is to keep your money and data safe.
And to achieve this, we’re always adding and refining security controls across our banking platform. Late last year, we wrapped up a major networking project which let us control internal traffic in our platform (read about it here). This gave us a lot of confidence that malicious code or an intruder compromising an individual microservice wouldn’t be able to hurt our customers.
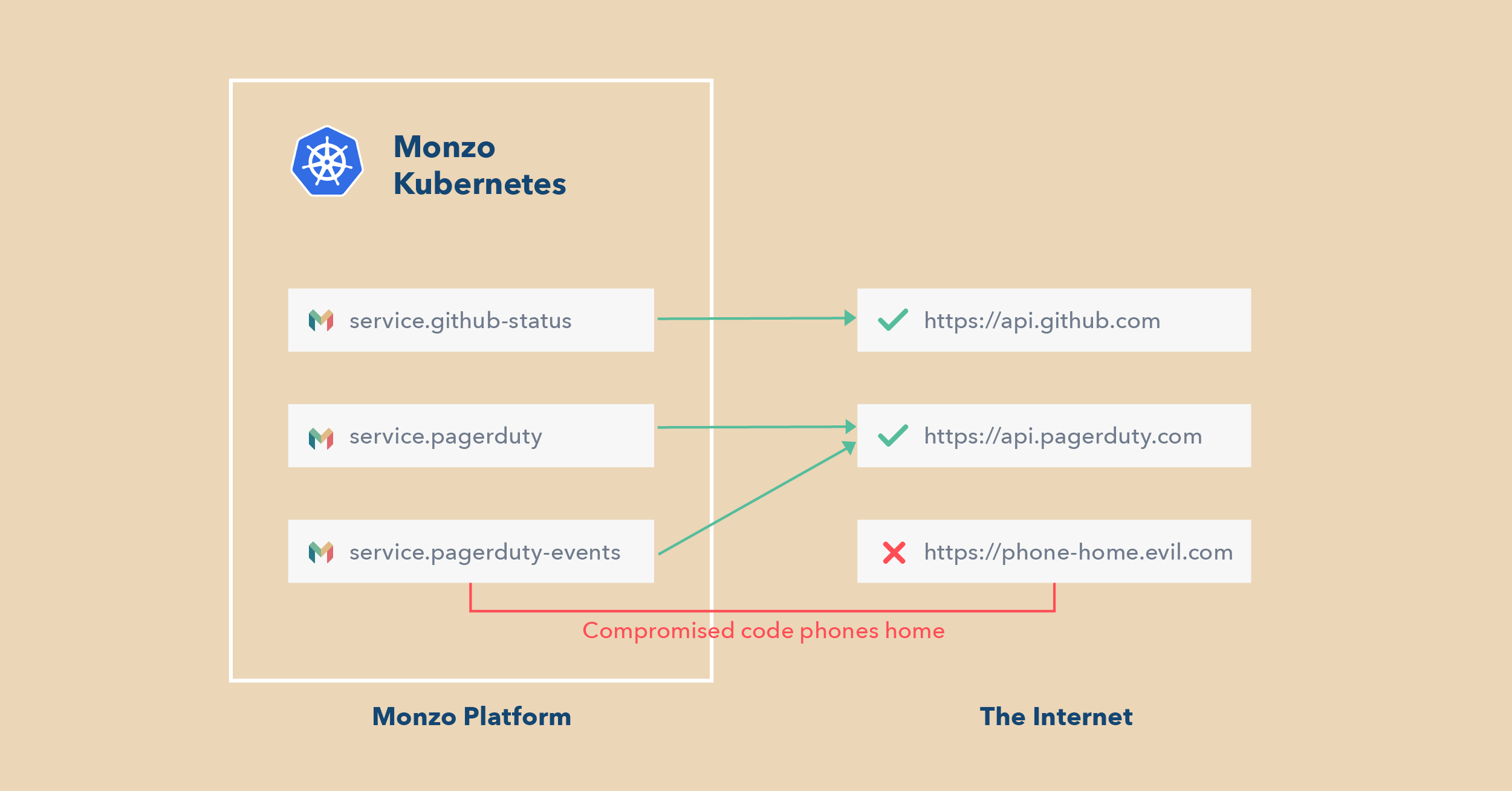
Since then, we’ve been thinking about how we can add similar security to network traffic leaving our platform. A lot of attacks begin with a compromised platform component ‘phoning home’ — that is, communicating with a computer outside of Monzo that is controlled by the attacker. Once this communication is established, the attacker can control the compromised service and attempt to infiltrate deeper into our platform.
We knew that if we could block that communication, we’d stand a better chance at stopping an attack in its tracks.
Source: monzo.com