Secure Control of Egress Traffic in Istio, part 3
Table of Contents

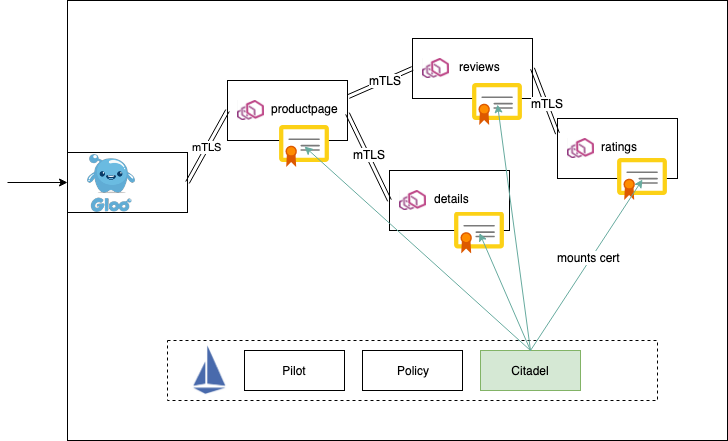
Welcome to part 3 in our series about secure control of egress traffic in Istio. In the first part in the series, I presented the attacks involving egress traffic and the requirements we collected for a secure control system for egress traffic. In the second part in the series, I presented the Istio way of securing egress traffic and showed how you can prevent the attacks using Istio.
In this installment, I compare secure control of egress traffic in Istio with alternative solutions such as using Kubernetes network policies and legacy egress proxies and firewalls. Finally, I describe the performance considerations regarding the secure control of egress traffic in Istio. First, let’s remember the requirements for egress traffic control we previously collected: Support of TLS with SNI or of TLS origination.
Monitor SNI and the source workload of every egress access. Define and enforce policies per cluster. Define and enforce policies per source, Kubernetes-aware.
Prevent tampering. Traffic control is transparent to the applications.
Source: istio.io