Crossplane v0.3 – accelerating support for more clouds and managed services
Table of Contents

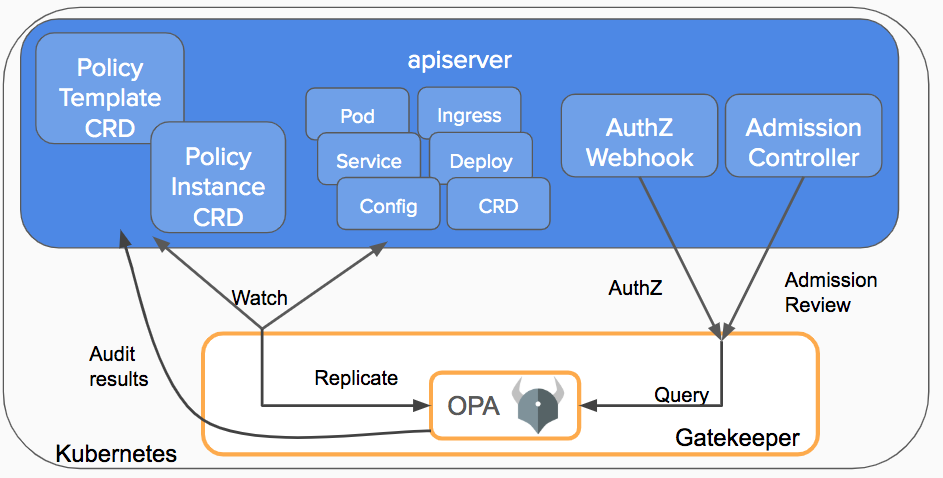
New developer guide, CLI tooling and enhanced out-of-tree Infra Stacks (GCP, AWS, Azure) enables the community to add support for more cloud providers, managed Kubernetes offerings, and fully-managed cloud services that can be hosted in your cloud of choice. The momentum keeps rolling forward with Crossplane community engagement around extending Crossplane to add support for additional cloud providers, managed Kubernetes offerings, and managed cloud services (DBaaS, Big Data, and more). It’s a busy time for us
and we’re very excited to have such a collaborative community! Here are just a few stats since the v0.2 release that show how quickly things are moving: There are so many changes in this release, we can’t tell you about all of them in a single post. We’ll give you the highlights here and then follow up with separate posts over the coming weeks, including all the details in the latest version of the crossplane.io/docs!
In this release we have enhanced the Infrastructure Stacks for GCP, AWS, and Azure to use a refined set of best-practices codified in a new crossplane-runtime and moved them out-of-tree where they can be extended or adapted by the community with different release schedules.
Source: crossplane.io