AWS OUTPERFORMS GCP IN THE 2018 CLOUD REPORT
Customers rely on us to help navigate the complexities of the increasingly competitive cloud wars. This inspired the 2018 Cloud Computing Report, where we benchmark performance, latency, CPU, network, I/O, and cost of AWS and GCP. Note: As of December 20, 2018, we have updated two sections in this report: Network Throughput and I/O Experiment. The updates do not change the relative performance of either cloud — however, it does narrow the gap. We are committed to building a cloud neutral product, and we run test clusters on all three leading US cloud providers. As we were testing features for our 2.1 release, we noticed something interesting: AWS offered 40% greater throughput than GCP.
Read moreENVOY PROXY AT REDDIT
Reddit’s engineering team and product complexity has seen significant growth over the last three years. Facilitating that growth has taken a lot of behind-the-scenes evolution of Reddit’s backend infrastructure. One major component has been adopting a service-oriented architecture, and a significant facet of that has been evolving service-to-service discovery and communication. As the number of services has grown, so has the complexity in how they interact with each other and legacy systems. Instead of debugging function and module calls within a monolithic application, engineers now need insight about RPCs among multiple services. Instead of focusing on common problems like exception handling and bad input, engineers also have to consider client request behaviors and defend appropriately with retry-handling, circuit-breaking and granular route control.
Read more8 EMERGING TRENDS IN CONTAINER ORCHESTRATION
Containerization is now officially mainstream. A quarter of Datadog’s total customer base has adopted Docker and other container technologies, and half of the companies with more than 1,000 hosts have done so. As containers take a more prominent place in the infrastructure landscape, we see our customers adding automation and orchestration to help manage their fleets of ephemeral containers. Across all infrastructure environments, our data shows increased usage of container orchestration technologies such as Kubernetes and Amazon Elastic Container Service (ECS). The companies running these technologies tend to have larger, far more dynamic deployments than companies running unorchestrated containers.
Read more8 EMERGING TRENDS IN CONTAINER ORCHESTRATION
Containerization is now officially mainstream. A quarter of Datadog’s total customer base has adopted Docker and other container technologies, and half of the companies with more than 1,000 hosts have done so. As containers take a more prominent place in the infrastructure landscape, we see our customers adding automation and orchestration to help manage their fleets of ephemeral containers. Across all infrastructure environments, our data shows increased usage of container orchestration technologies such as Kubernetes and Amazon Elastic Container Service (ECS). The companies running these technologies tend to have larger, far more dynamic deployments than companies running unorchestrated containers.
Read moreWHAT KAGGLERS ARE USING FOR TEXT CLASSIFICATION
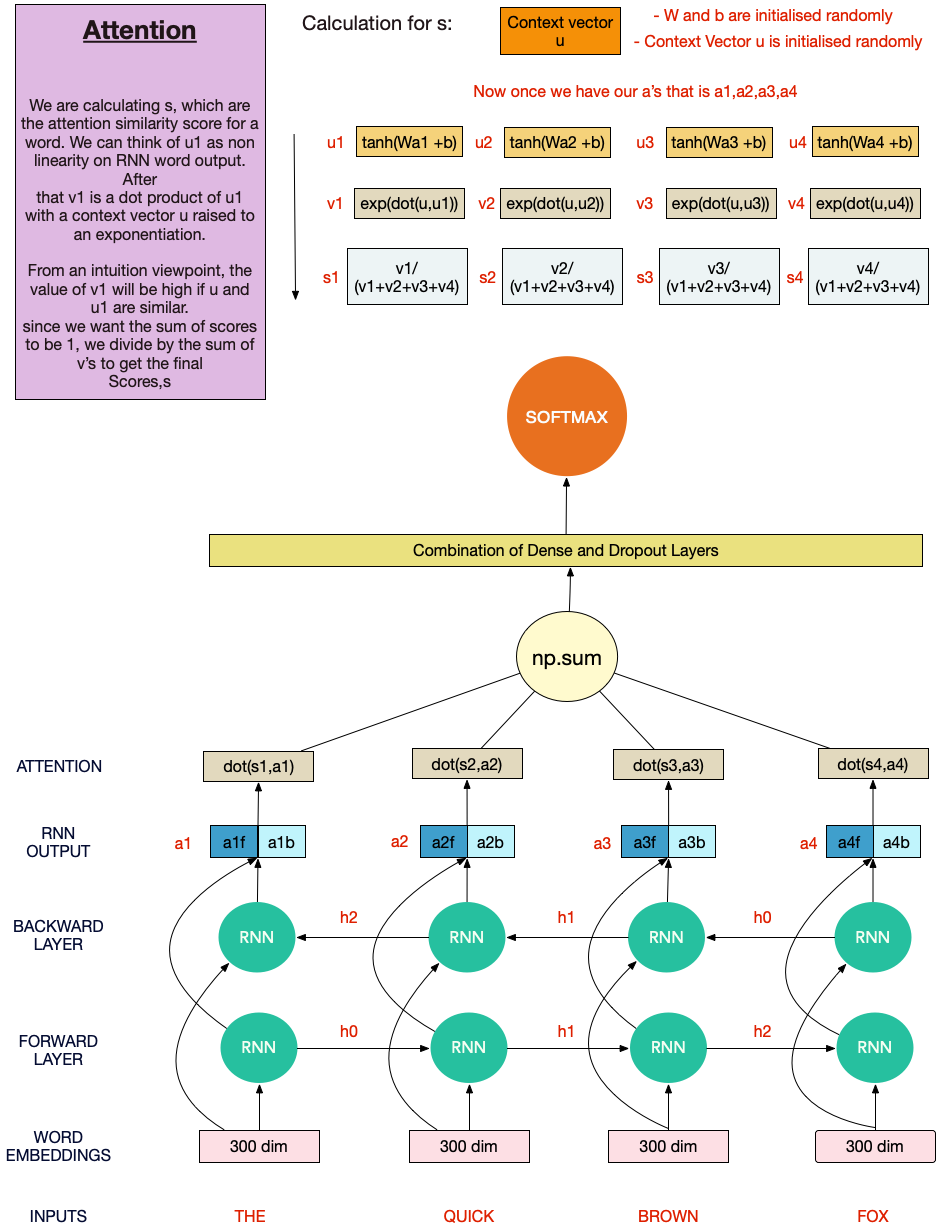 With the problem of Image Classification is more or less solved by Deep learning, Text Classification is the next new developing theme in deep learning. For those who don’t know, Text classification is a common task in natural language processing, which transforms a sequence of text of indefinite length into a category of text. How could you use that? Source: mlwhiz.com
VAULT LEARNING RESOURCES: 1.0, AUTO-UNSEAL, AGENT, KUBERNETES
Learn from hands-on labs to build proficiency with Vault 1.0, auto-unseal, Kubernetes, and other secrets management features. Source: hashicorp.com
OBSERVABILITY AT SCALE: BUILDING UBER’S ALERTING ECOSYSTEM
Uber’s software architectures consists of thousands of microservices that empower teams to iterate quickly and support our company’s global growth. These microservices support a variety of solutions, such as mobile applications, internal and infrastructure services, and products along with complex configurations that affect these products at city and sub-city levels. To maintain our growth and architecture, Uber’s Observability team built a robust, scalable metrics and alerting pipeline responsible for detecting, mitigating, and notifying engineers of issues with their services as soon as they occur.
Read moreISTIO MULTICLUSTER
Istio Multicluster is a feature of Istio–the basis of Red Hat OpenShift Service Mesh–that allows for the extension of the service mesh across multiple Kubernetes or Red Hat OpenShift clusters. The primary goal of this feature is to enable control of services deployed across multiple clusters with a single control plane. The main requirement for Istio multicluster to work is that the pods in the mesh and the Istio control plane can talk to each other.
Read moreKUBERNETES FEDERATION V2
With datacenters spread across the globe, users are increasingly looking at ways to spread their applications and services across multiple locales or clusters. This need is driven by multiple use cases: from providing high availability, spreading load across multiple clusters while being resilient to individual cluster failures; to avoiding provider lock-in by using hybrid cloud … With datacenters spread across the globe, users are increasingly looking at ways to spread their applications and services across multiple locales or clusters.
Read moreDNS OVER TLS: ENCRYPTING DNS END-TO-END
As a first step toward encrypting the last portion of internet traffic that has historically been cleartext, we have partnered with Cloudflare DNS on a pilot project. This pilot takes advantage of the benefits of Transport Layer Security (TLS) — a widely adopted and proven mechanism for providing authentication and confidentiality between two parties over an insecure channel — in conjunction with DNS. This solution, DNS over TLS (DoT), would encrypt and authenticate the remaining portion of web traffic.
Read more