Setting up Kubernetes Network Policies
Table of Contents
![]()
The container orchestrator war is over, and Kubernetes has won. With companies large and small rapidly adopting the platform, security has emerged as an important concern — partly because of the learning curve inherent in understanding any new infrastructure, and partly because of recently announced vulnerabilities. Kubernetes brings another security dynamic to the table — its defaults are geared towards making it easy for users to get up and running quickly, as well as being backward compatible with earlier releases of Kubernetes that lacked important security features.
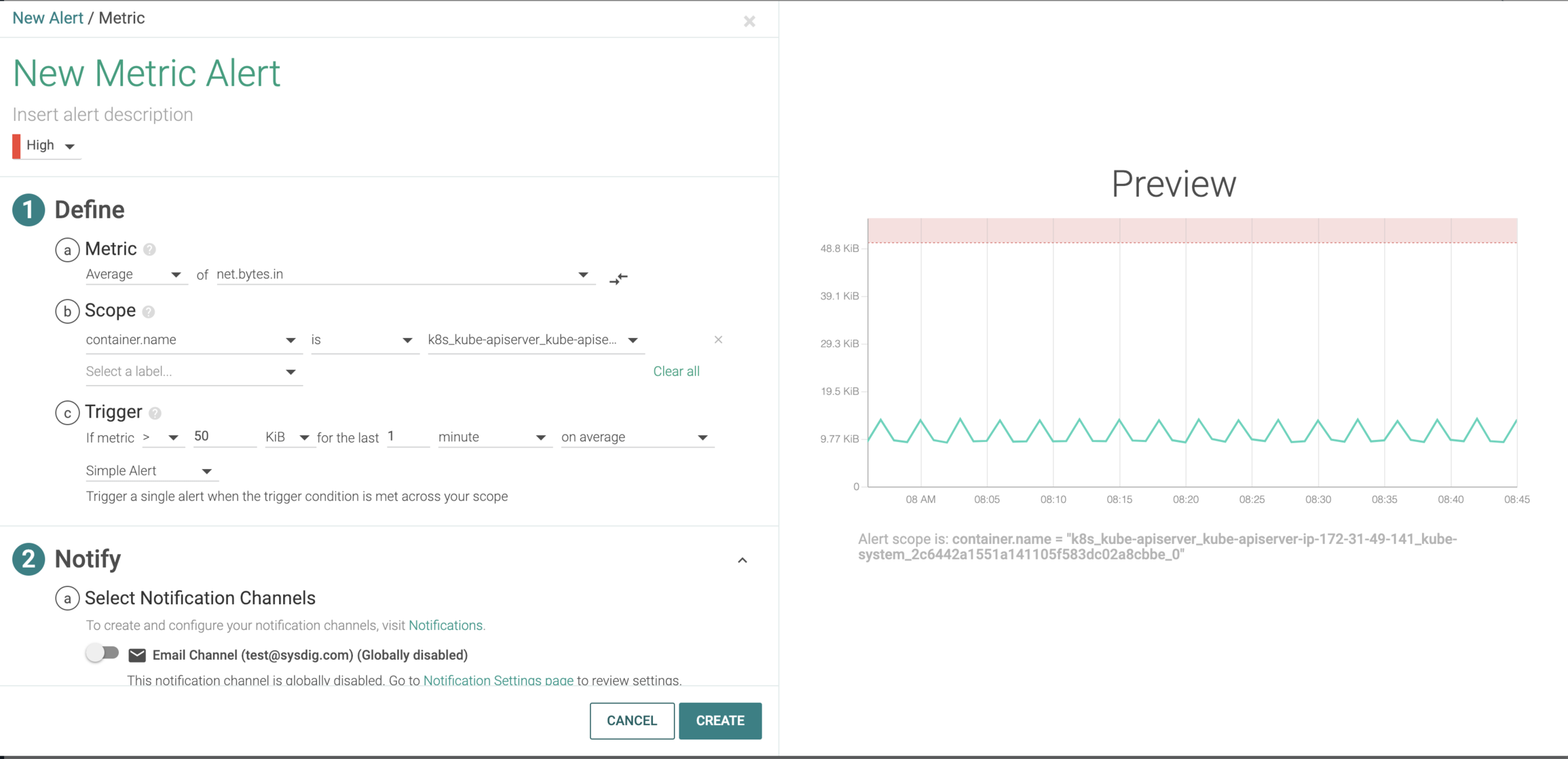
Consequently, many important Kubernetes configurations are not secure by default. One important configuration that demands attention from a security perspective is the network policies feature. Network policies specify how groups of pods are allowed to communicate with each other and other network endpoints.
You can think of them as the Kubernetes equivalent of a firewall. On a side note, if you haven’t already done so, upgrade to the latest Kubernetes version because some of the most critical Kubernetes security issues have been addressed by recent Kubernetes updates. We lay out here a step-by-step guide on how to set up network policies.
The network policy spec is intricate, and it can be difficult to understand and use correctly. In this guide, we provide recommendations that significantly improve security. Users can easily apply these recommendations without needing to know the spec in detail.
Source: cncf.io