Unplugging From Digital Controls to Safeguard Power Grids
Late last week, the U.S. House of Representatives passed legislation to mandate federal research on a radically ‘retro’approach to protect power grids from cyber attack: unplugging or otherwise isolating the most criticalequipment from grid operators’ digital control systems. Angus King, an independent senator from Maine whose identical bill passedthe Senate last month, says such a managed retreat from networked controls may berequired to thwart the grid’s most sophisticated online adversaries. Grid cyber experts say the Securing Energy Infrastructure Act moving through Congress isa particular testament toMichael Assante, a gifted and passionate cybersecurity expert whodied earlier this monthfrom leukaemia at the age of 48.
Read More
How to detect Kubernetes vulnerability CVE-2019-11246 using Falco.
A recent CNCF-sponsored Kubernetes security audit uncovered CVE-2019-11246, a high-severity vulnerability affecting the command-line kubectl tool. If exploited, it could lead to a directory traversal, allowing a malicious container to replace or create files on a user’s workstation. This vulnerability stemmed from an incomplete fix of a previously disclosed vulnerability (CVE-2019-1002101).
Read More
33(+) Kubernetes security tools
Kubernetes image scanning Kubernetes runtime security Kubernetes network security Image distribution and secrets management Kubernetes security audit End-to-end commercial security tools Join our live session to learn more! Kubernetes security tools … there are so freaking many of them; with different purposes, scopes and licenses. That’s why we decided to create this Kubernetes security tools list, including open source projects and commercial platforms from different vendors, to help you choose the ones that look more interesting to you and guide you in the right direction depending on your Kubernetes security needs.
Read More
I’m Not A Robot!
There is no one way to secure your API that fits all situations. But, you can learn the schemes, study how the biggest social networks are dealing with it and find out the industry standard; then apply it to your project in the way you see fit. At the end of this article, you’ll have a clear understanding of the different schemes.
Read More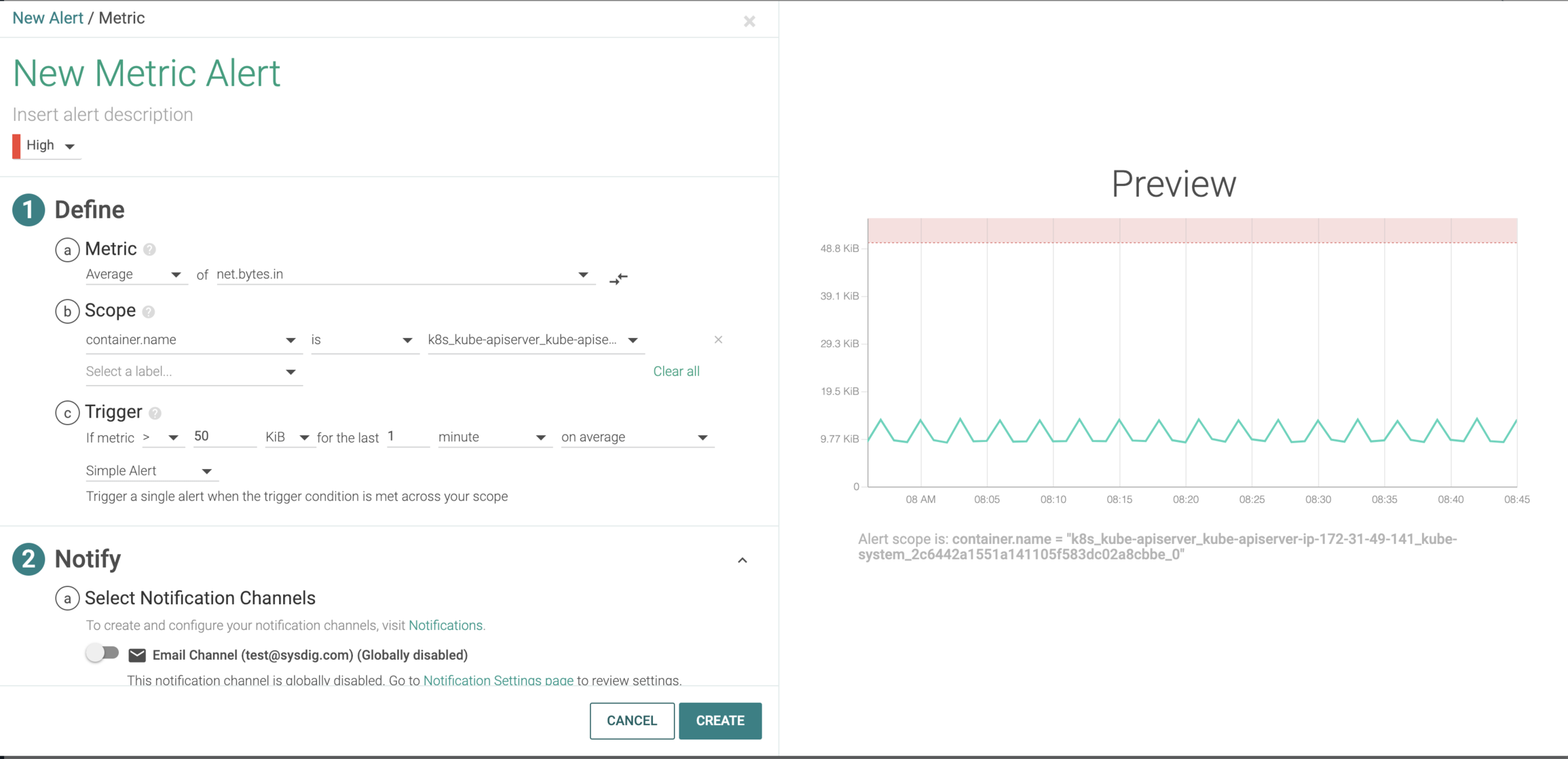
Detecting the Kubernetes API server DoS vulnerability (CVE-2019-1002100).
Recently, a new Kubernetes related vulnerability was announced that affected the kube-apiserver. This was a denial of service vulnerability where authorized users with write permissions could overload the API server as it is handling requests. The issue is categorized as a medium severity (CVSS score of 6.5) and can be resolved by upgrading the kube-apiserver to v1.11.8, v1.12.6, or v1.13.4.
Read More
Docker and Kubernetes in high security environments
This is brief summary of parts of my master’s thesis and the conclusions to draw from it. This medium-story focuses on containerized application isolation. The thesis also covers segmentation of cluster networks in Kubernetes which is not discussed in this story.
Read More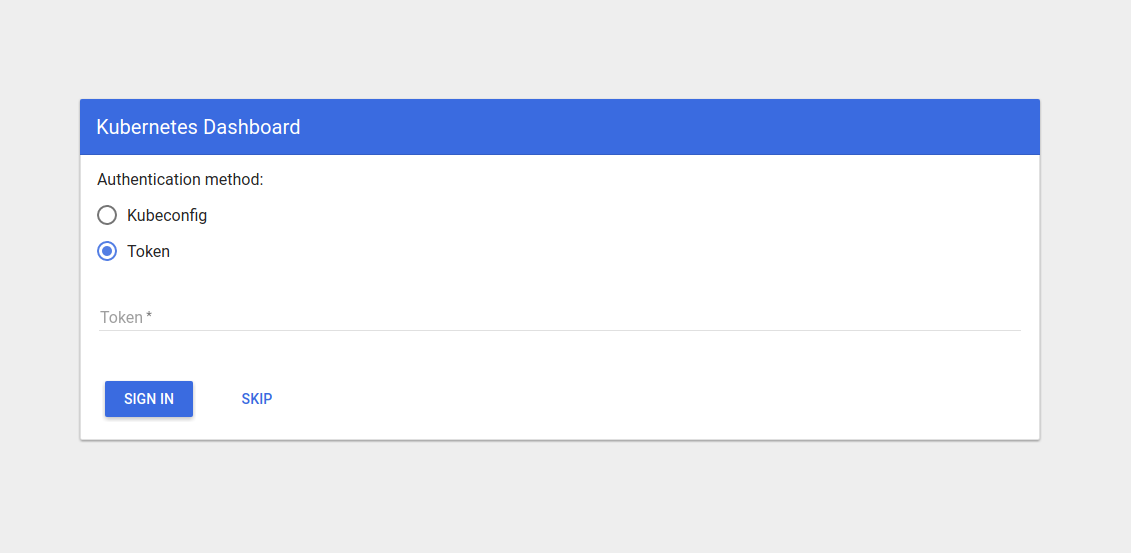
CVE-2018-18264 Privilege escalation through Kubernetes dashboard
A recently disclosed vulnerability in Kubernetes dashboard (CVE-2018-18264) exposes secrets to unauthenticated users. In this blog post we’ll explore some key takeaways regarding monitoring privilege escalation on Kubernetes. The Kubernetes dashboard is a web based user interface that allows users to manage applications and resources within the cluster.
Read More
Running Kubernetes in the Federal Government
Tackling security compliance is a long and challenging process for agencies, systems integrators, and vendors trying to launch new information systems in the federal government. Each new information system must go through the Risk Management Framework (RMF) created by the National Institute of Standards and Technology (NIST) in order to obtain authority to operate (ATO). This process is often long and tedious and can last for over a year.
Read More
Vault Learning Resources: 1.0, Auto-unseal, Agent, Kubernetes
Learn from hands-on labs to build proficiency with Vault 1.0, auto-unseal, Kubernetes, and other secrets management features.
Read More
DNS over TLS: Encrypting DNS end-to-end
As a first step toward encrypting the last portion of internet traffic that has historically been cleartext, we have partnered with Cloudflare DNS on a pilot project. This pilot takes advantage of the benefits of Transport Layer Security (TLS) — a widely adopted and proven mechanism for providing authentication and confidentiality between two parties over an insecure channel — in conjunction with DNS. This solution, DNS over TLS (DoT), would encrypt and authenticate the remaining portion of web traffic.
Read More
Moving from Kube2Iam to Kiam
At Ibotta, we chose kube2iam to assign AWS IAM Roles to containers running in our Kubernetes cluster. Lately, we’ve run into some issues with it—specifically when running a job that scores all of our service repos. This spins up a number of pods in parallel and has often failed to correctly access roles.
Read More
Kubernetes’ first major security hole discovered
Kubernetes has become the most popular cloud container orchestration system by far, so it was only a matter of time until its first major security hole was discovered. And the bug, CVE-2018-1002105, aka the Kubernetes privilege escalation flaw, is a doozy. It’s a CVSS 9.8 critical security hole.
Read More