News
- Home /
- News

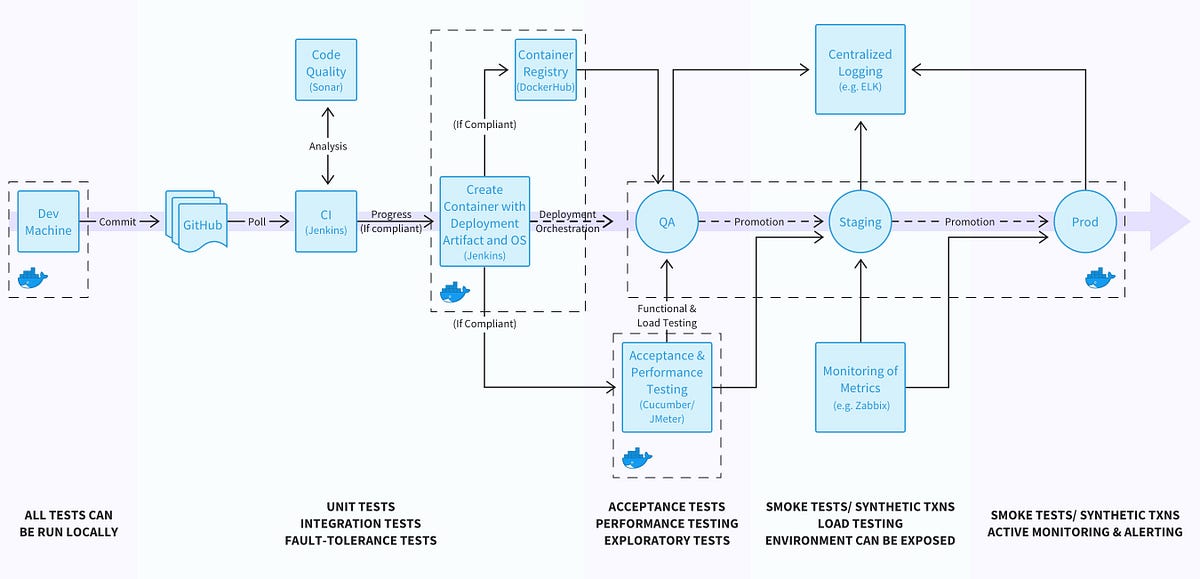
How to detect Kubernetes vulnerability CVE-2019-11246 using Falco.
A recent CNCF-sponsored Kubernetes security audit uncovered CVE-2019-11246, a high-severity vulnerability affecting the command-line kubectl tool. If exploited, it could lead to a directory traversal, allowing a malicious container to replace or create files on a user’s workstation. This vulnerability stemmed from an incomplete fix of a previously disclosed vulnerability (CVE-2019-1002101).
Read More
33(+) Kubernetes security tools
Kubernetes image scanning Kubernetes runtime security Kubernetes network security Image distribution and secrets management Kubernetes security audit End-to-end commercial security tools Join our live session to learn more! Kubernetes security tools … there are so freaking many of them; with different purposes, scopes and licenses. That’s why we decided to create this Kubernetes security tools list, including open source projects and commercial platforms from different vendors, to help you choose the ones that look more interesting to you and guide you in the right direction depending on your Kubernetes security needs.
Read More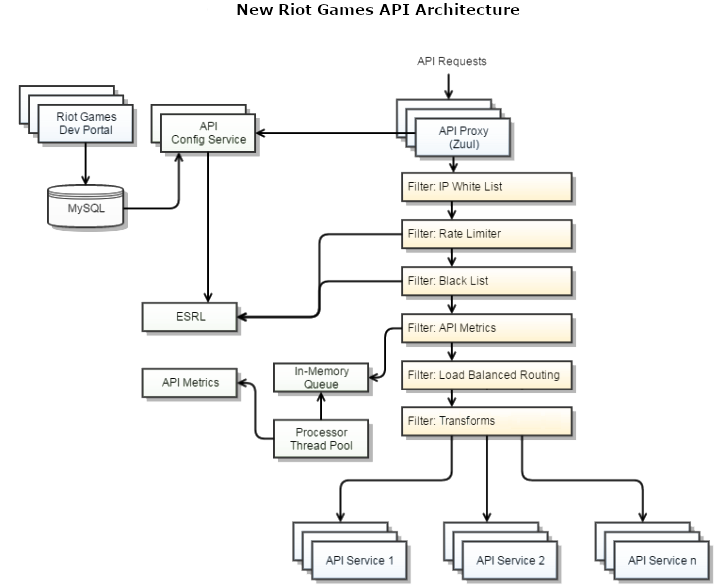
The Riot Games API: Transforms
Hello all, Leigh Estes, aka RiotSchmick, here. I’m a software engineer at Riot Games working on the Riot Developer Experience team. Our responsibilities include providing the edge infrastructure that supports both internal and external developers.
Read More
Benchmarking Service Mesh Performance
Service meshes add a lot of functionality to application deployments, including traffic policies, observability, and secure communication. But adding a service mesh to your environment comes at a cost, whether that’s time (added latency) or resources (CPU cycles). To make an informed decision on whether a service mesh is right for your use case, it’s important to evaluate how your application performs when deployed with a service mesh.
Read More
Toward a bastion-less world
Using a bastion or jump server has been a common way to allow access to secure infrastructure in your virtual private cloud (VPC) and is integrated into several Quick Starts. Amazon Web Services (AWS) has recently released two new features that allow us to connect securely to private infrastructure without the need for a bastion host. This greatly improves your security and audit posture by centralizing access control and reducing inbound access.
Read More
A Technical Analysis of the Capital One Hack
The recent disclosure of yet another cloud security misconfiguration leading to the loss of sensitive personal information made the headlines this past week. This particular incident came with a bit more information from the indictment of the accused party, allowing us to piece together the revealed data and take an educated guess as to what may have transpired leading up to the loss of over 100 million credit card applications and 100 thousand social security numbers. At the root of the hack lies a common refrain: the misconfiguration of cloud infrastructure resources allowed an unauthorized user to elevate her privileges and compromise sensitive documents.
Read MoreCategories
Tags
- 3dprinting
- 5g
- Ai
- Alexa
- Algorithm
- Amazon
- Ambassador
- Ansible
- Api
- Apple
- Appmesh
- Appswitch
- Argo
- Art
- Artificialintelligence
- Astronomy
- Augmentedreality
- Aurora
- Australia
- Authentication
- Automation
- Aws
- Azure
- Bayesian
- Bgp
- Bigdata
- Bioengineering
- Biology
- Blackhole
- Blockchain
- Brain
- Build
- Buildah
- Business
- Cancer
- Casestudy
- China
- Chip
- Cia
- Cicd
- Cilium
- Climatechange
- Cloud
- Cloudnative
- Cncf
- Codeanalysis
- Computing
- Connectedcars
- Consul
- Container
- Coredns
- Creativity
- Crio
- Crispr
- Cubesat
- Culture
- Dashboard
- Data
- Database
- Datacenter
- Datadog
- Datascience
- Dataset
- Deeplearning
- Deepmind
- Developer
- Development
- Devops
- Digitalcurrency
- Dna
- Dns
- Docker
- Drone
- Ec2
- Economy
- Education
- Einstein
- Eks
- Elasticsearch
- Electricvehicle
- Emdrive
- Energy
- Engineering
- Envoy
- Erlang
- Esa
- Facialrecognition
- Fail
- Falco
- Fashion
- Fda
- Federation
- Fitnessfunction
- Flair
- Fluentd
- Flutter
- Flyingcars
- Food
- Funny
- Gaia
- Gcp
- Gdpr
- Genome
- Geography
- Geopolitics
- Gis
- Git
- Github
- Gitlab
- Gitops
- Gloo
- Go
- Gps
- Grafana
- Graphene
- Graphql
- Grpc
- Hashicorp
- Health
- Healthcare
- Helm
- Hft
- Highavailability
- History
- Hurricane
- Hyperloop
- Iac
- Ibm
- Image
- Imagerecognition
- Ingress
- Innovation
- Intel
- Ios
- Iot
- Istio
- Jaeger
- Jenkins
- Kafka
- Keras
- Kiali
- Knative
- Kubedb
- Kubeedge
- Kubernetes
- Lambda
- Latinamerica
- Legal
- Lidar
- Linkerd
- Linux
- Lyft
- M3
- Machinelearning
- Mars
- Math
- Microservices
- Microsoft
- Mobile
- Mongo
- Monitoring
- Moon
- Multicloud
- Multicluster
- Mysql
- Nanorobot
- Nasa
- Nature
- Navigation
- Network
- Networking
- Newrelic
- News
- Nextjs
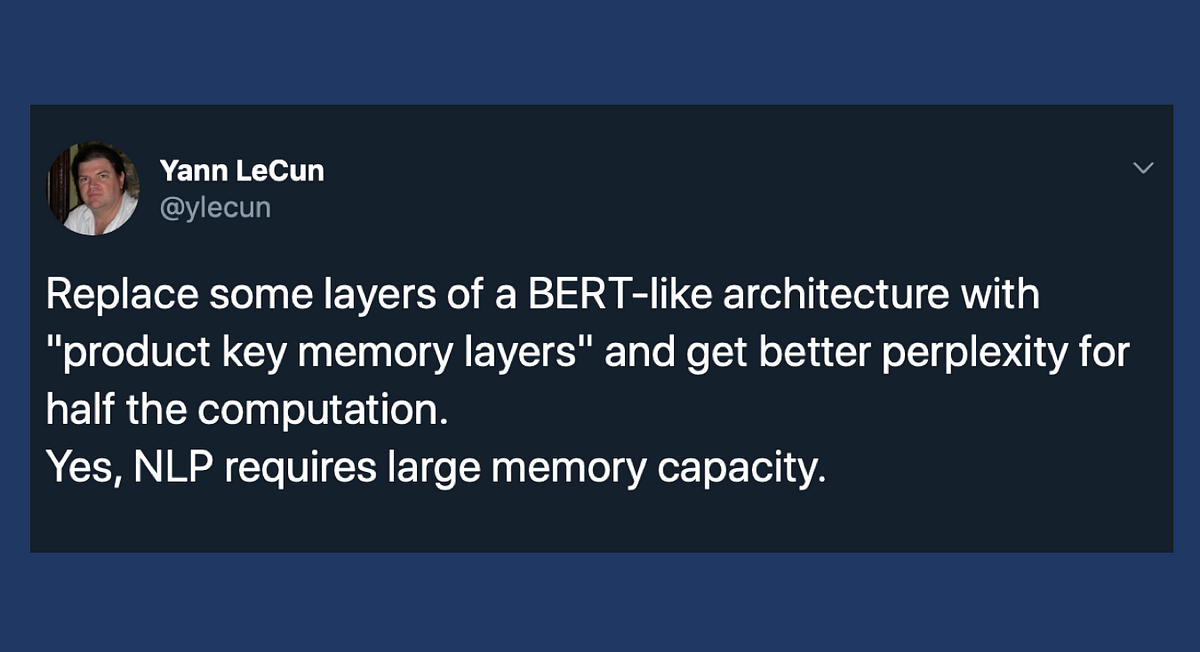
- Nlp
- Nlu
- Observability
- Onnx
- Onpremise
- Opencensus
- Openmetrics
- Opentracing
- Openwhisk
- Operator
- Opinion
- Outage
- Perforce
- Performance
- Pharma
- Philosophy
- Physics
- Podman
- Postgres
- Pprof
- Presto
- Privacy
- Programming
- Prometheus
- Protocol
- Psychology
- Python
- Pytorch
- Qa
- Quantum
- Quantumcomputing
- Qubit
- React
- Recycling
- Redis
- Release
- Renewable
- Research
- Resilience
- Rnn
- Robot
- Rook
- Scalability
- Scaling
- Science
- Secrets
- Security
- Selfdrivingcars
- Sentry
- Serverless
- Servicemesh
- Slack
- Smartgrid
- Smi
- Sociology
- Space
- Spacex
- Spacy
- Spark
- Spinnaker
- Sql
- Squash
- Sre
- Startup
- Storage
- Study
- Success
- Swift
- Sysdig
- Tailwind
- Technology
- Tensorflow
- Terraform
- Tesla
- Testcategory1
- Textclassification
- Traefik
- Training
- Transportation
- Troubleshooting
- Uber
- Ubi
- Vault
- Velero
- Versioncontrol
- Video
- Virtualreality
- Vision
- Visualization
- Vitess
- Warfare
- Wd
- Web
- Weird
- Wikipedia